Threats
RAWRR uses the Risks-Vulnerabilities-Recommendations framework and therefore threat and risk management is one of the first logical steps. Each threat can be assigned a level of impact on the organization’s work as well as a level of the probability of occurrence. The basic features of RAWRR related to threats are:
If you have started RAWRR by importing a file or loading the test values, it is convenient that you can carefully review the preloaded information before creating or editing any item. To see the full list of threats you can click on “All” in the lower right next to the phrase “Rows per page”. You can also select to view five (5), ten (10), or fifteen (15) items per page.
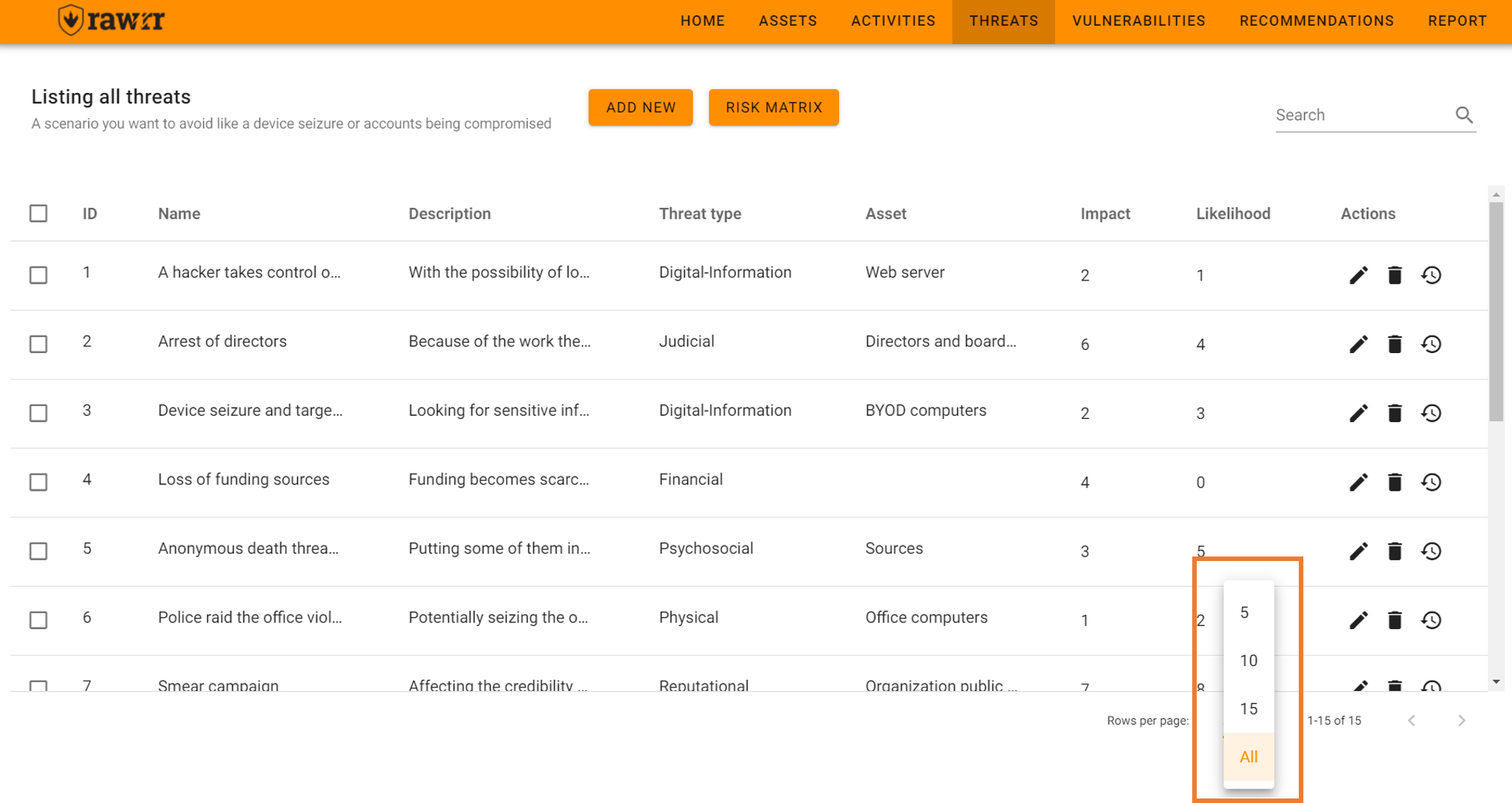
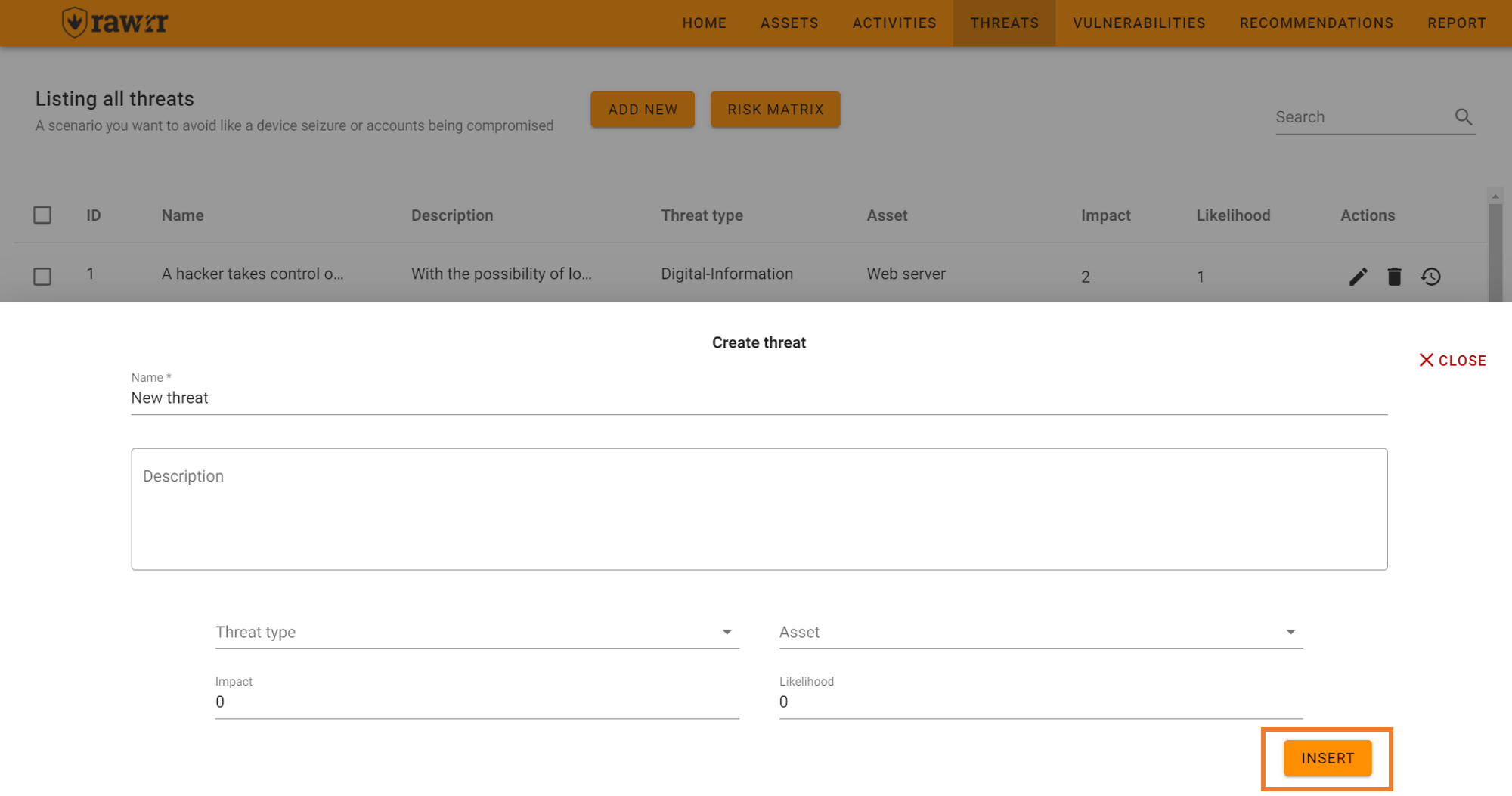
To add threats click “Add new” top left and complete the fields: name, description, type of threat, asset, impact and probability
When you are done click on “Insert”.
To edit, click on the pencil icon located to the right of each threat that appears in the pre-existing list.
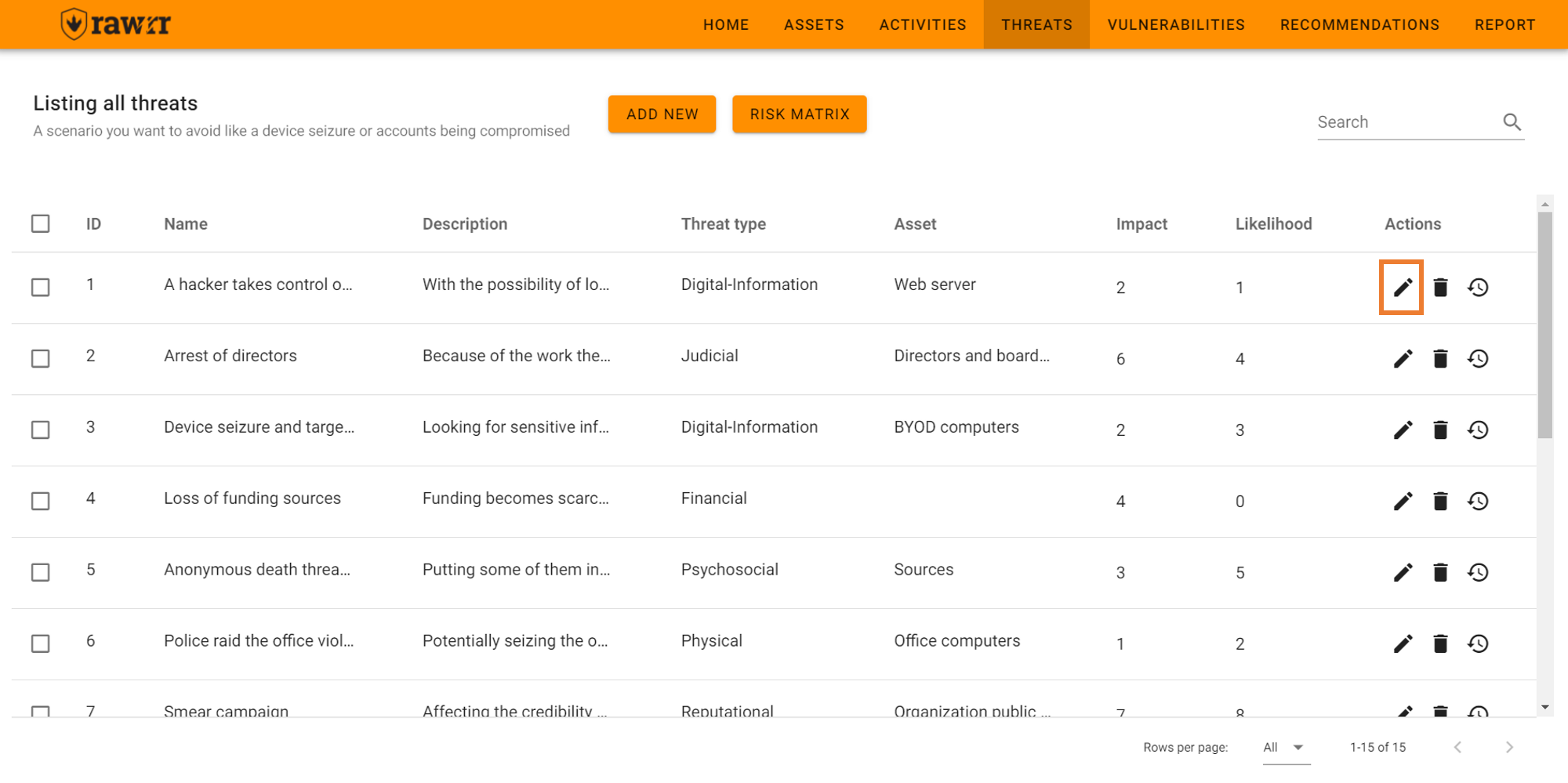
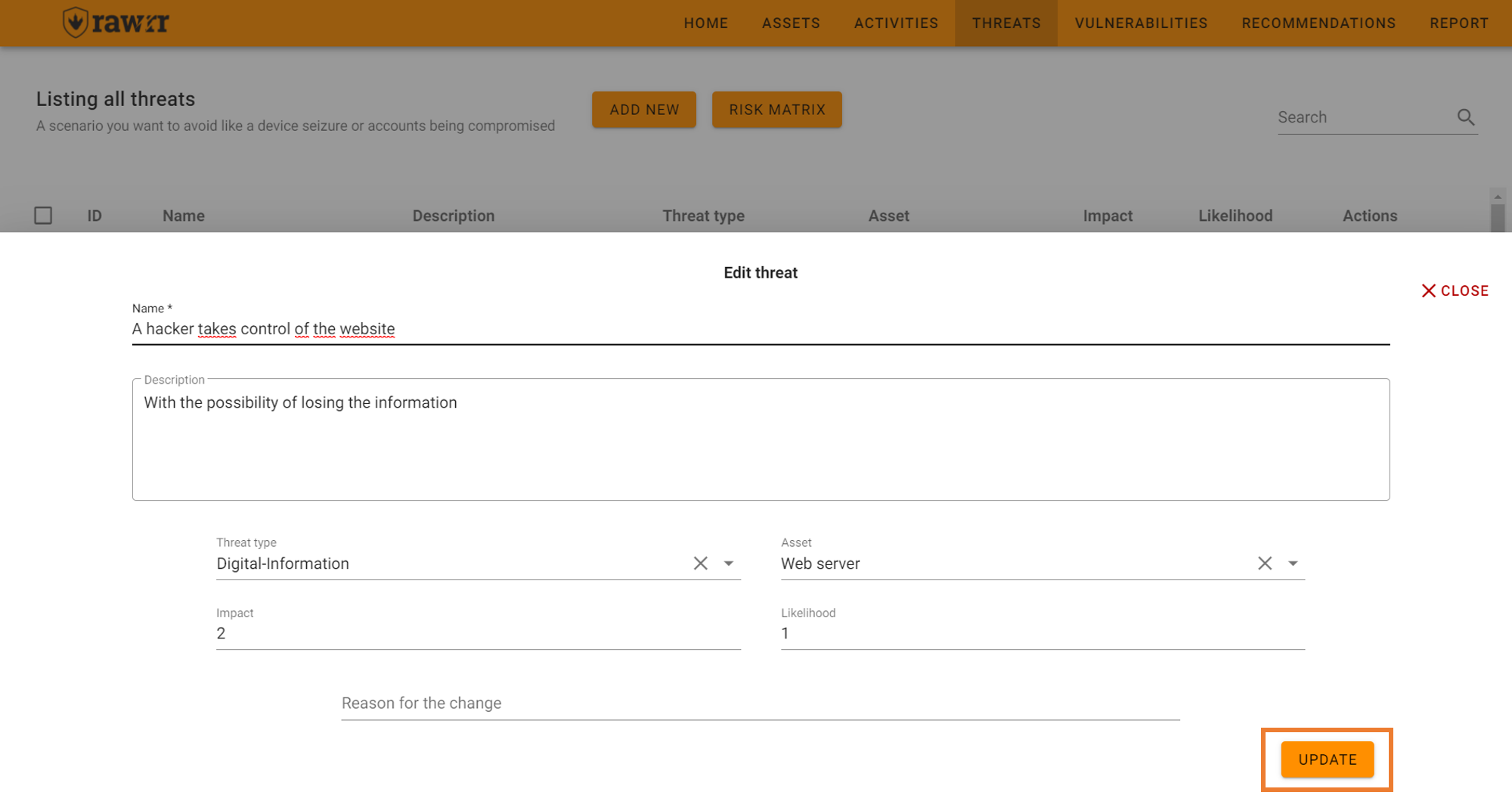
When you finish editing the name, description, threat type, asset, impact and/or probability fields, click “Update” to save the changes to the threat you selected.
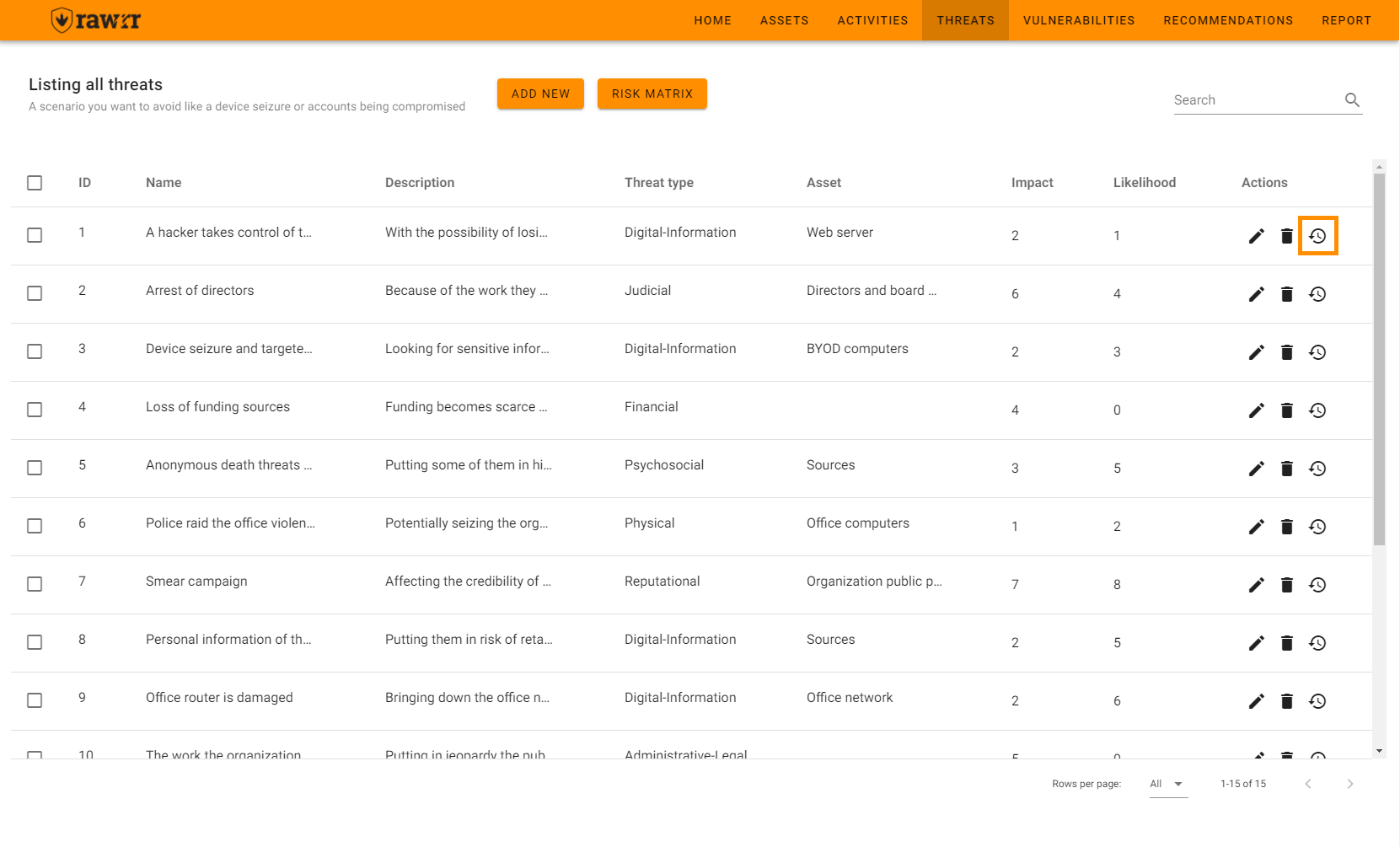
To see the timeline of when a threat was created or edited, click on the watch icon located to the right of each threat that appears in the pre-existing list.
On this screen, you can see the current data of the threat you selected: ID, Name, Description, Type, Asset, Impact and Likelihood.
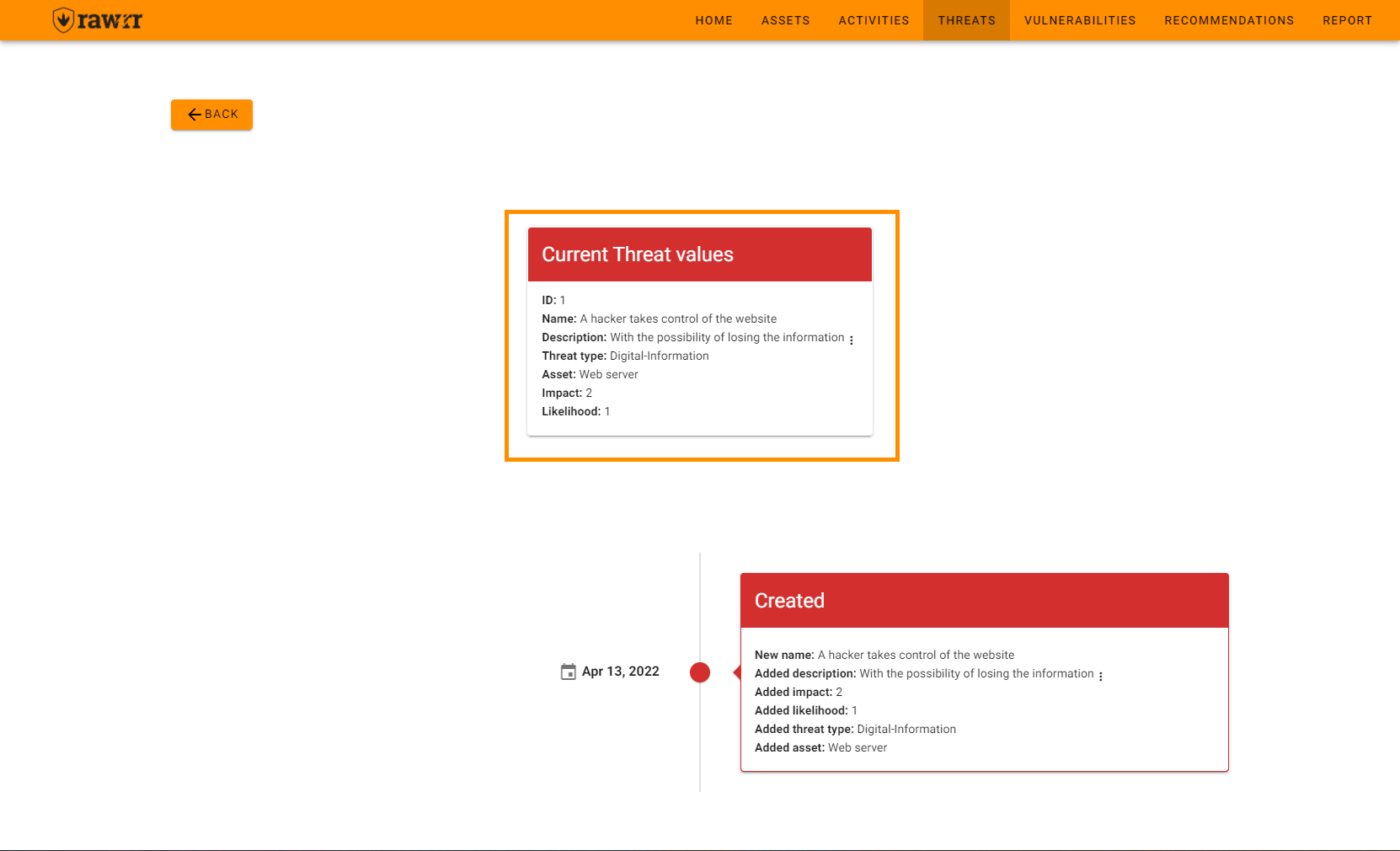
Also, you will be able to see the dates on which the threat was created or edited, and what information had any change.
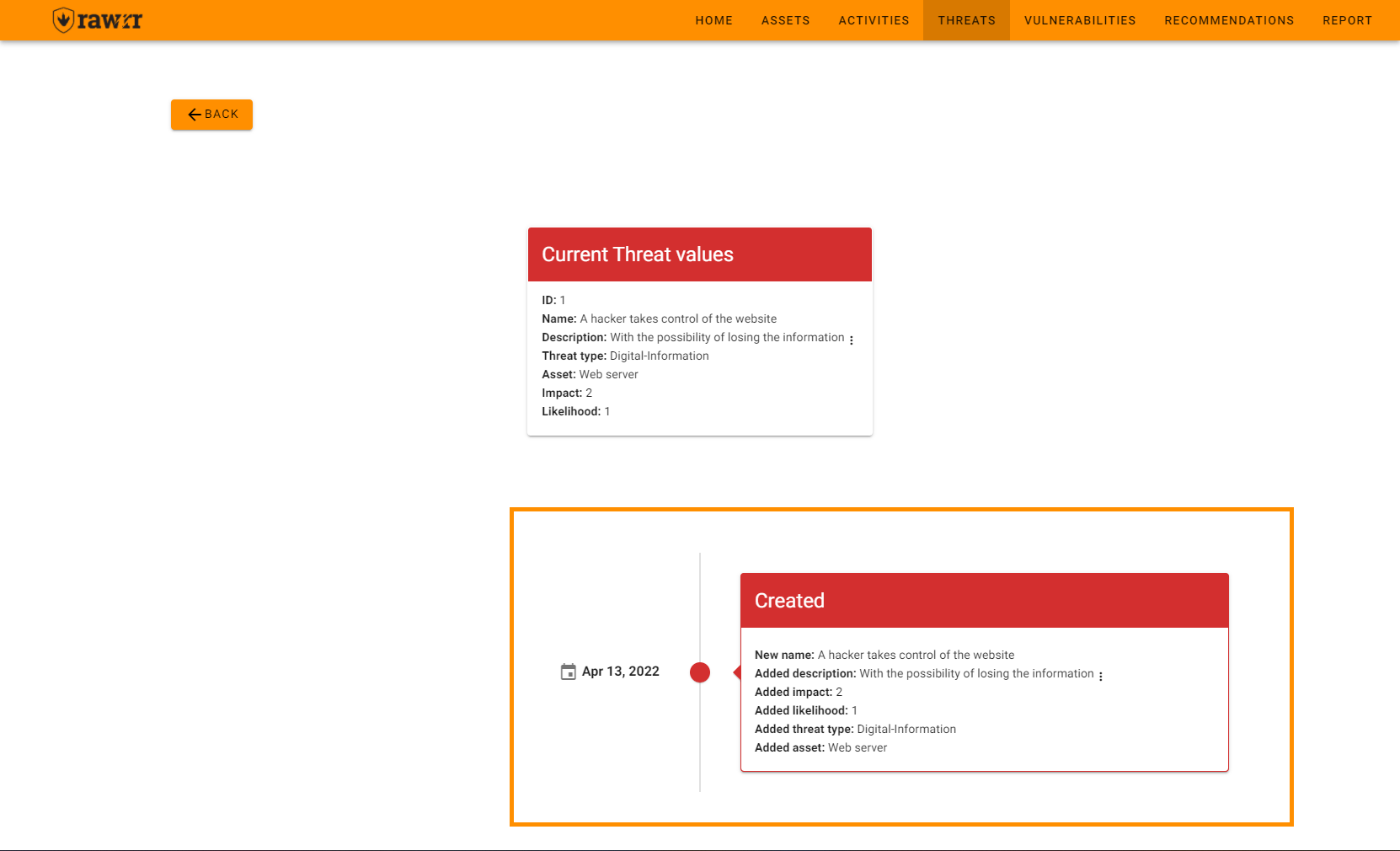
To return to the previous menu, click on the “Back” button, located in the upper left corner of the screen.
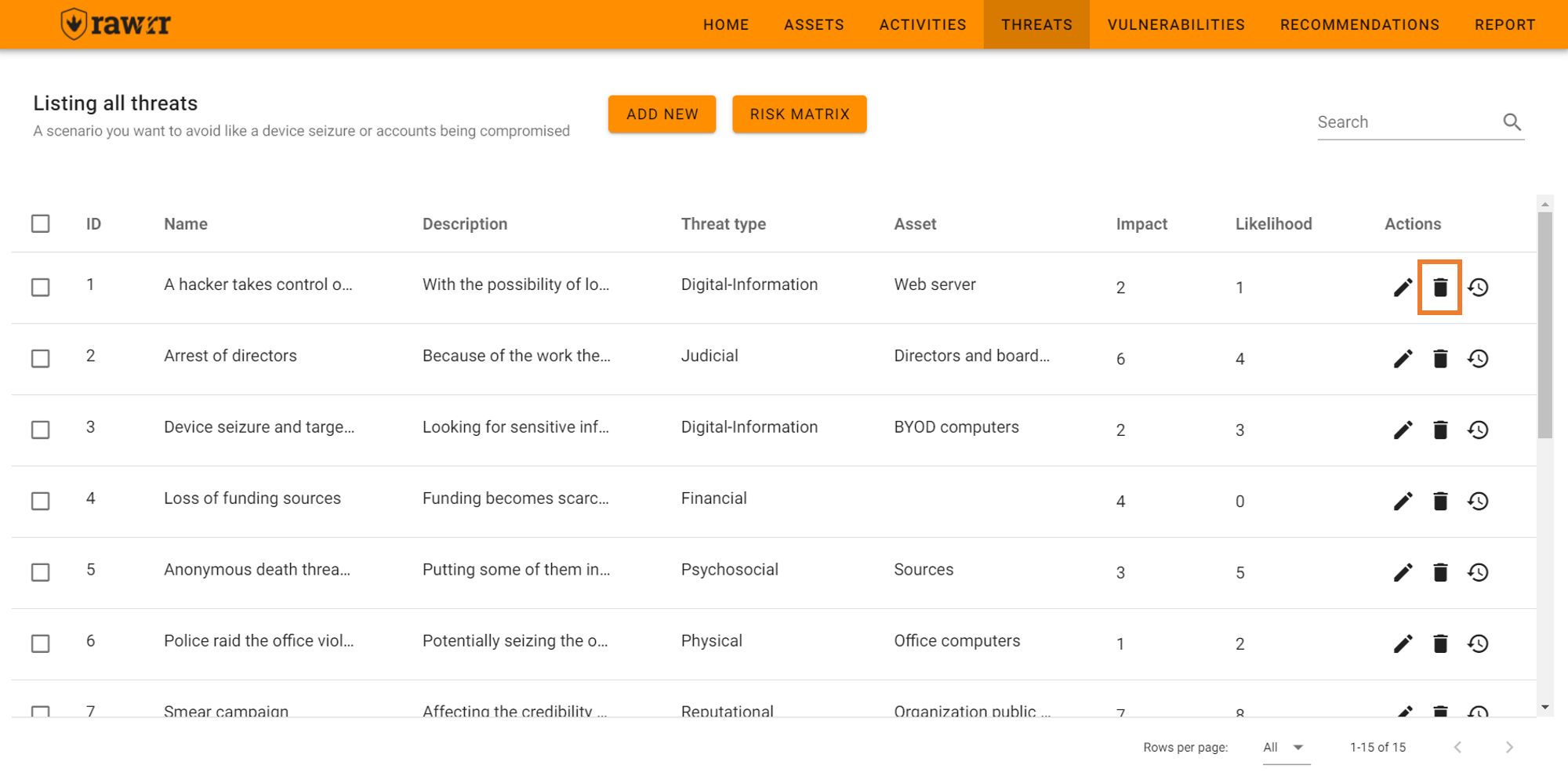
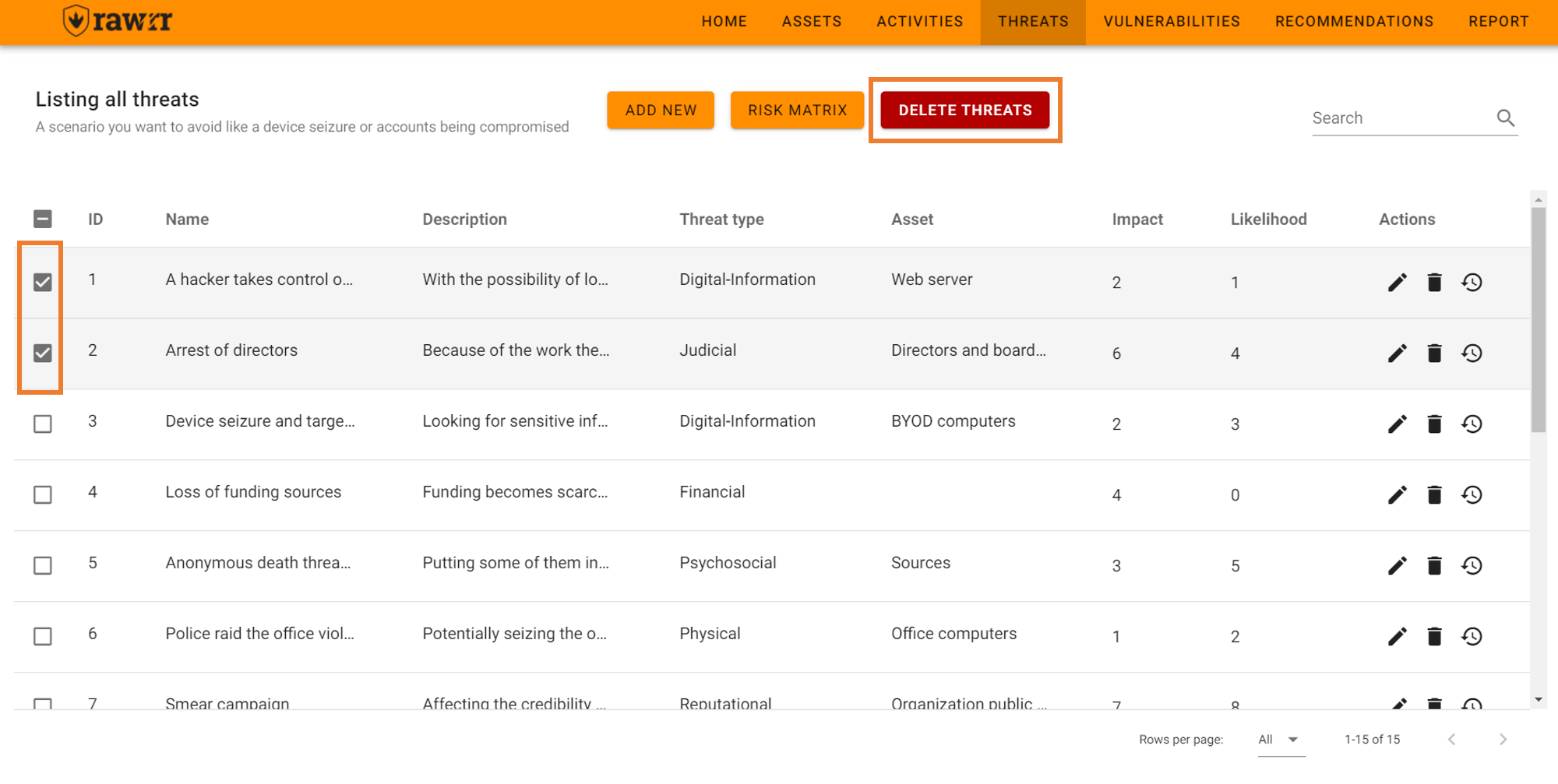
If you want to delete a threat from the list, click on the trash can icon located to the right of each threat that appears in the pre-existing list.
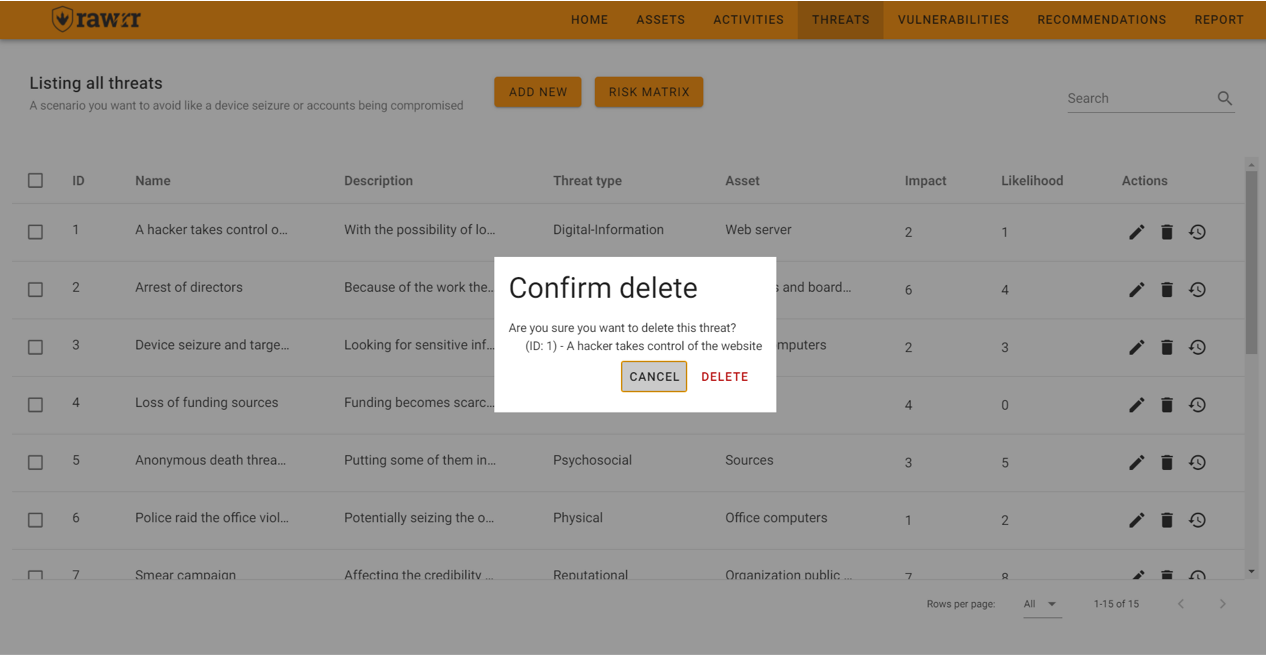
When you click, a confirmation message will appear. If you agree to remove the threat, click “Delete”.
You can also delete multiple threats by selecting them in the left box and then clicking “Delete Threats”.
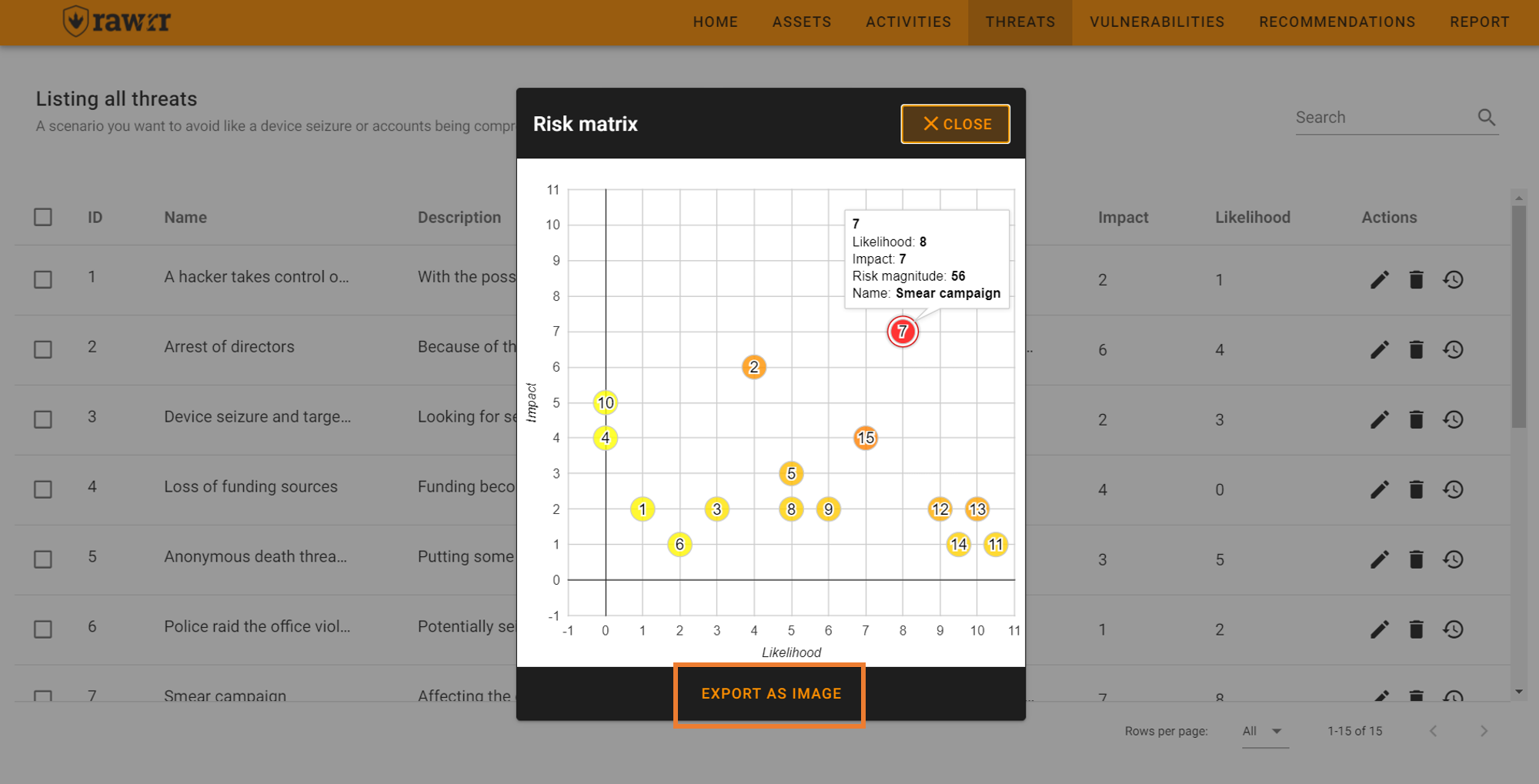
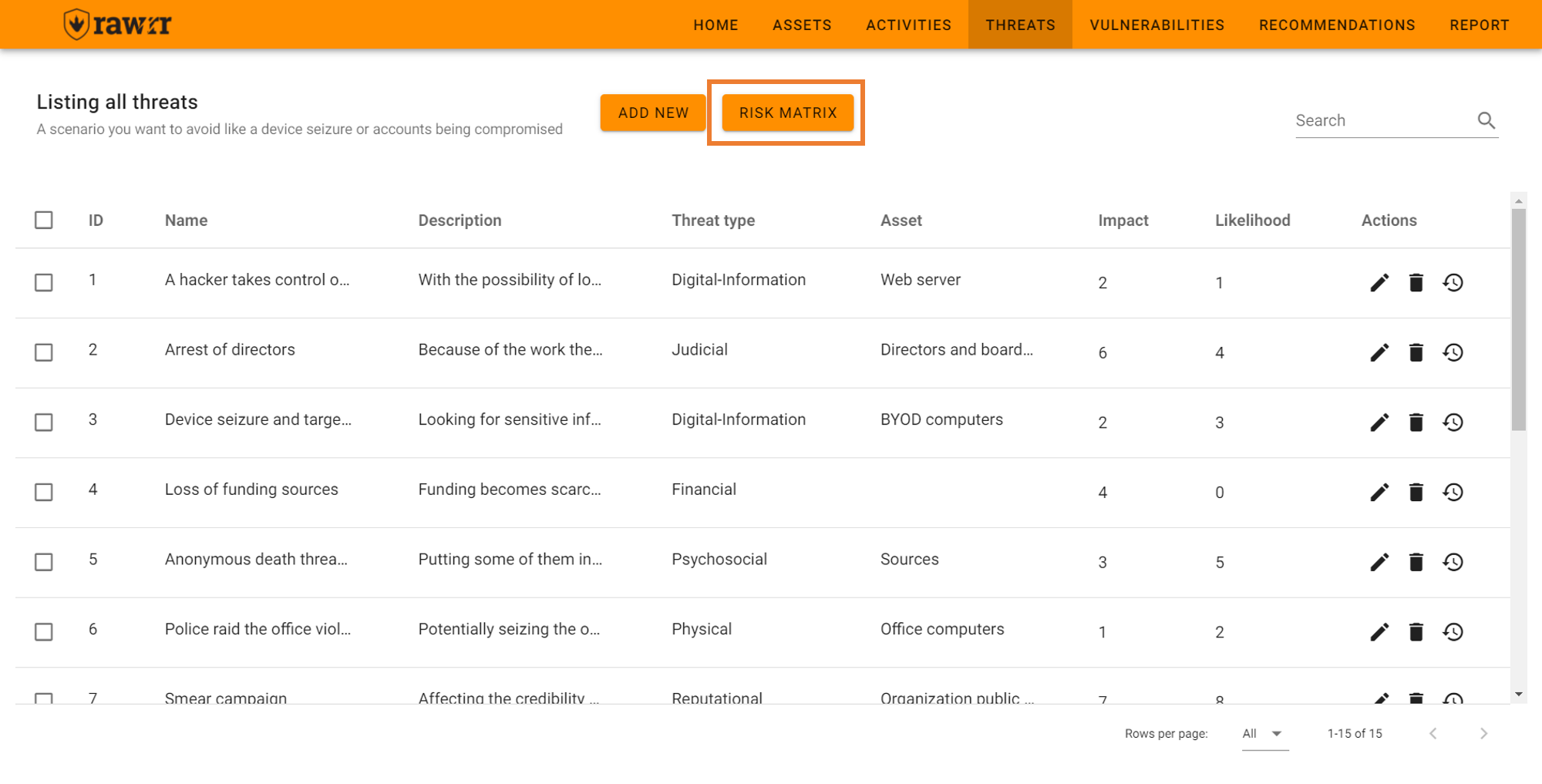
At the top in the middle you will find the “Risk Matrix” button. You can click at any time during the loading of the threats, or at the end of their identification, to see the graph that identifies each threat with a number and positions it on the graph according to its impact and probability to build the risk matrix of the organization you are evaluating.
To see the full name of a threat (and the rest of the associated data), you can hover your cursor over the number that identifies the threat.