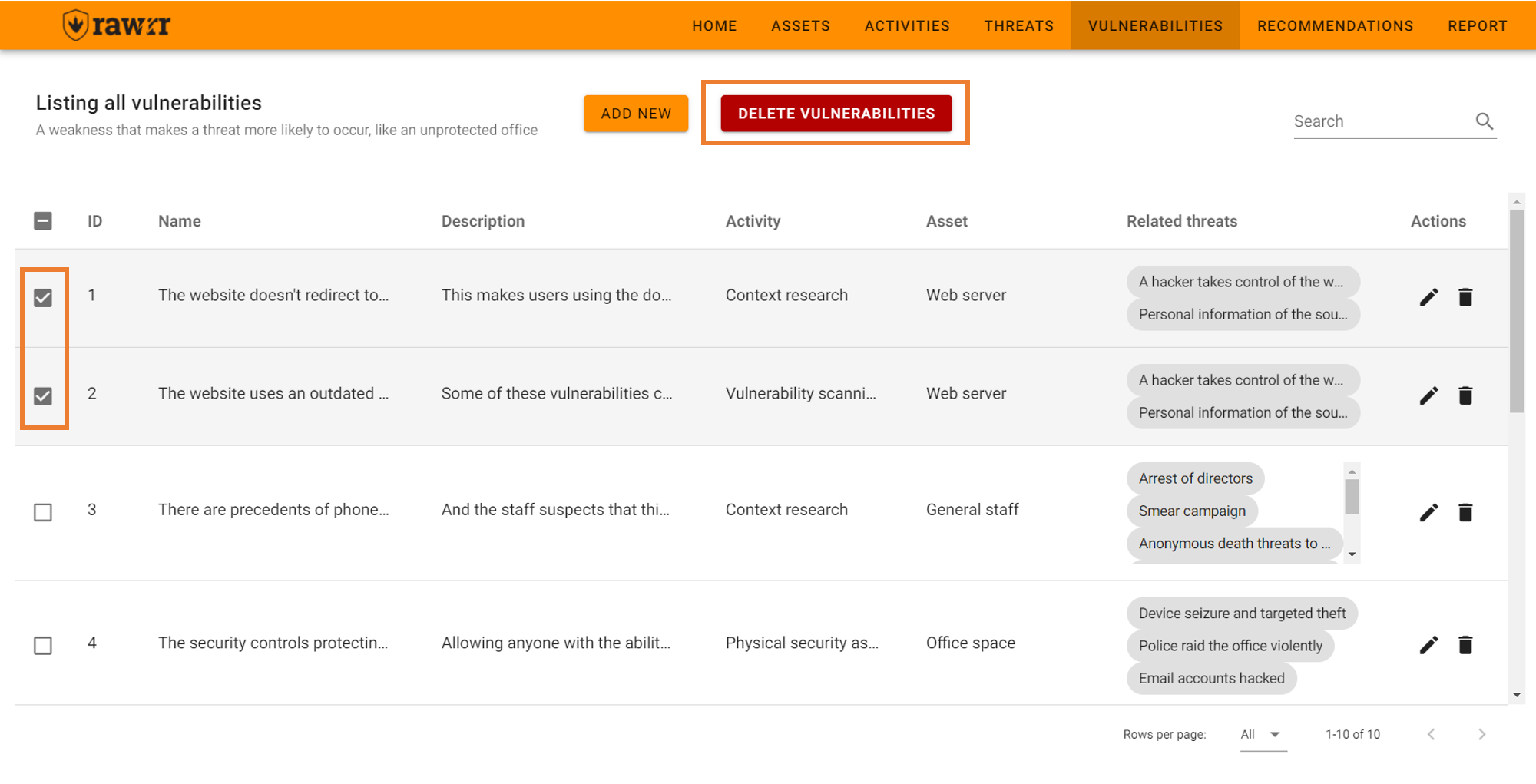
Vulnerabilities
One result of the assessment activities is to find vulnerabilities. They can be specified and linked to the activities that generated them and the related risks. The basic functions of RAWRR related to vulnerabilities are:
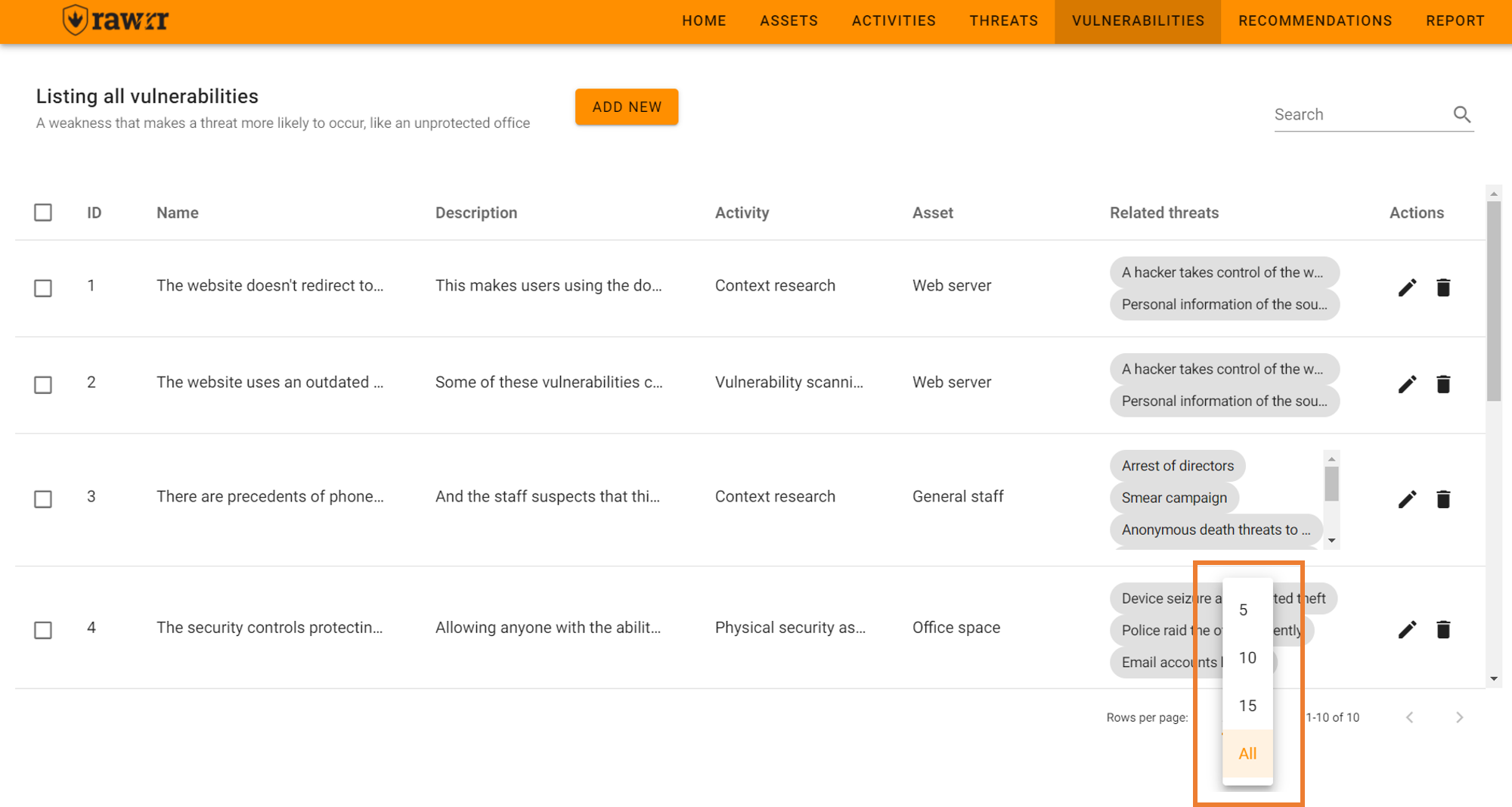
If you have started RAWRR by importing a file or loading the test values, it is convenient that you can carefully review the preloaded information before creating or editing any element. To see the full list of vulnerabilities you can click on “All” in the lower right next to the phrase “Rows per page”. You can also select to view five (5), ten (10), or fifteen (15) items per page.
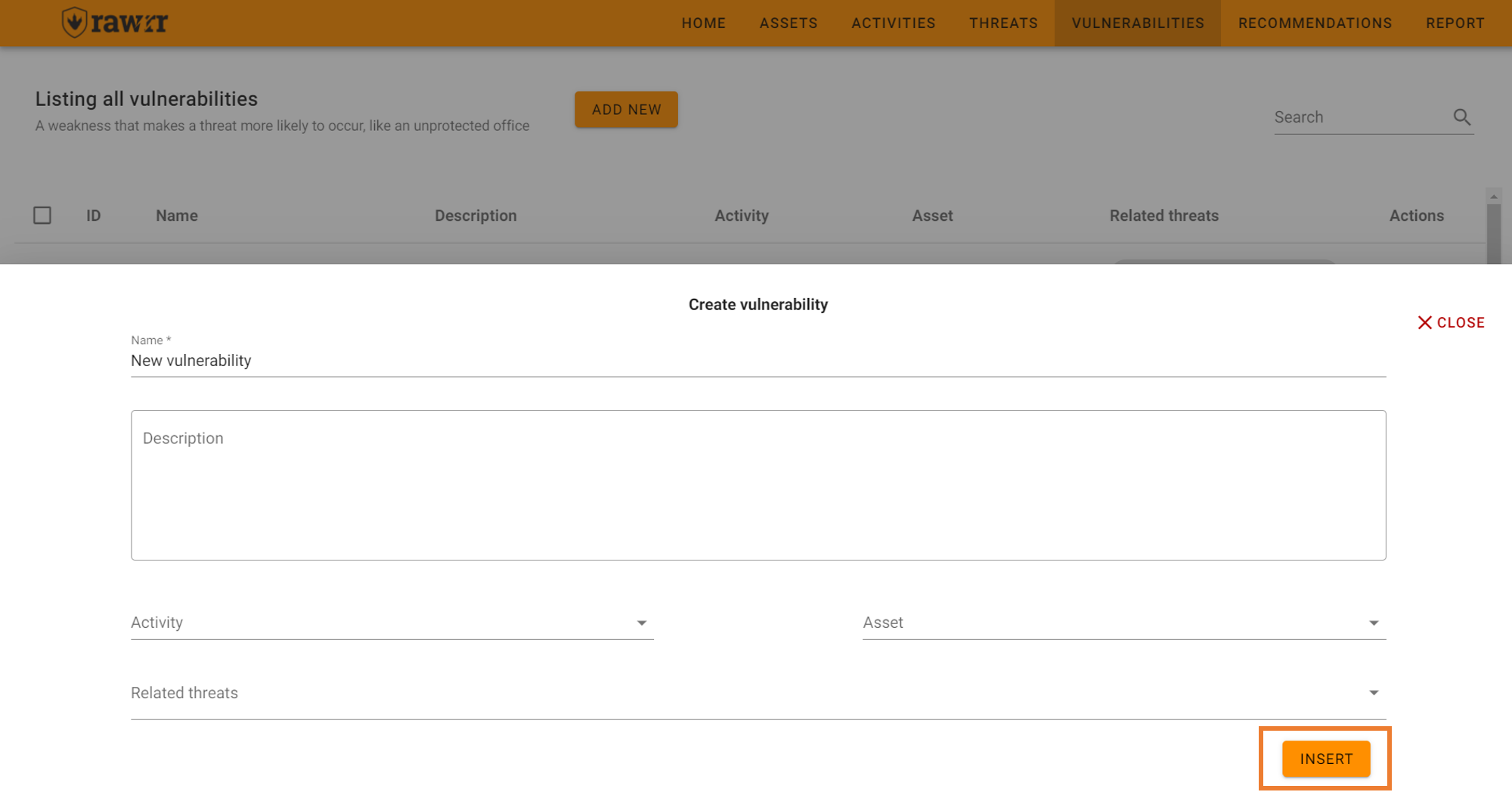
To add vulnerabilities click “Add new” top left and complete the fields that appear on the form: name, description, threat assessment activity and active.
The “Assessment activity” list allows you to associate a vulnerability of the organization to an activity because vulnerabilities are detected during the execution of an activity. In the same sense, the “Threat” list allows associating a vulnerability to one or more threats of the organization.
When you are done click on “Insert”.
To edit, click on the pencil icon located to the right of each vulnerability that appears in the pre-existing list.
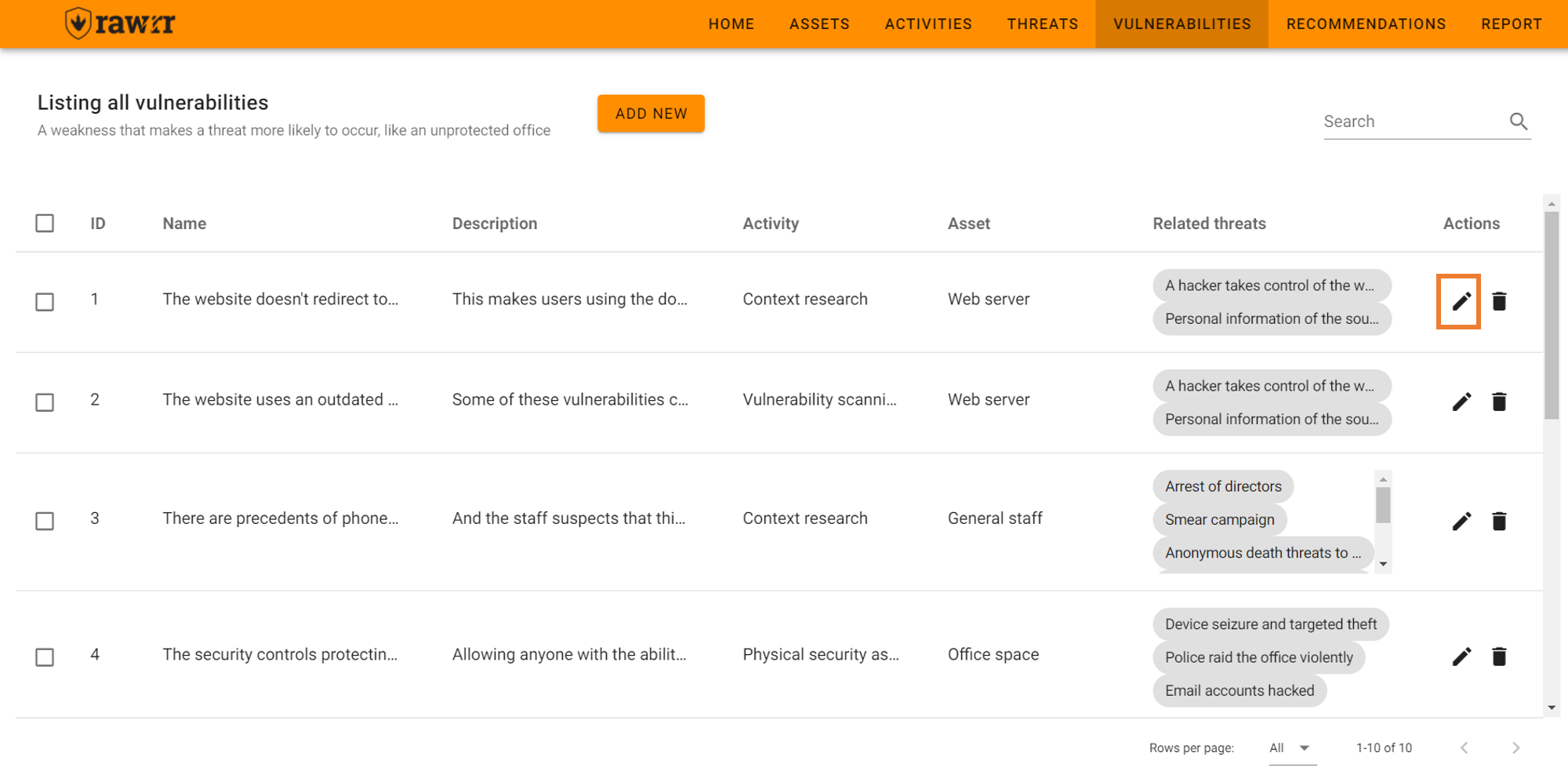
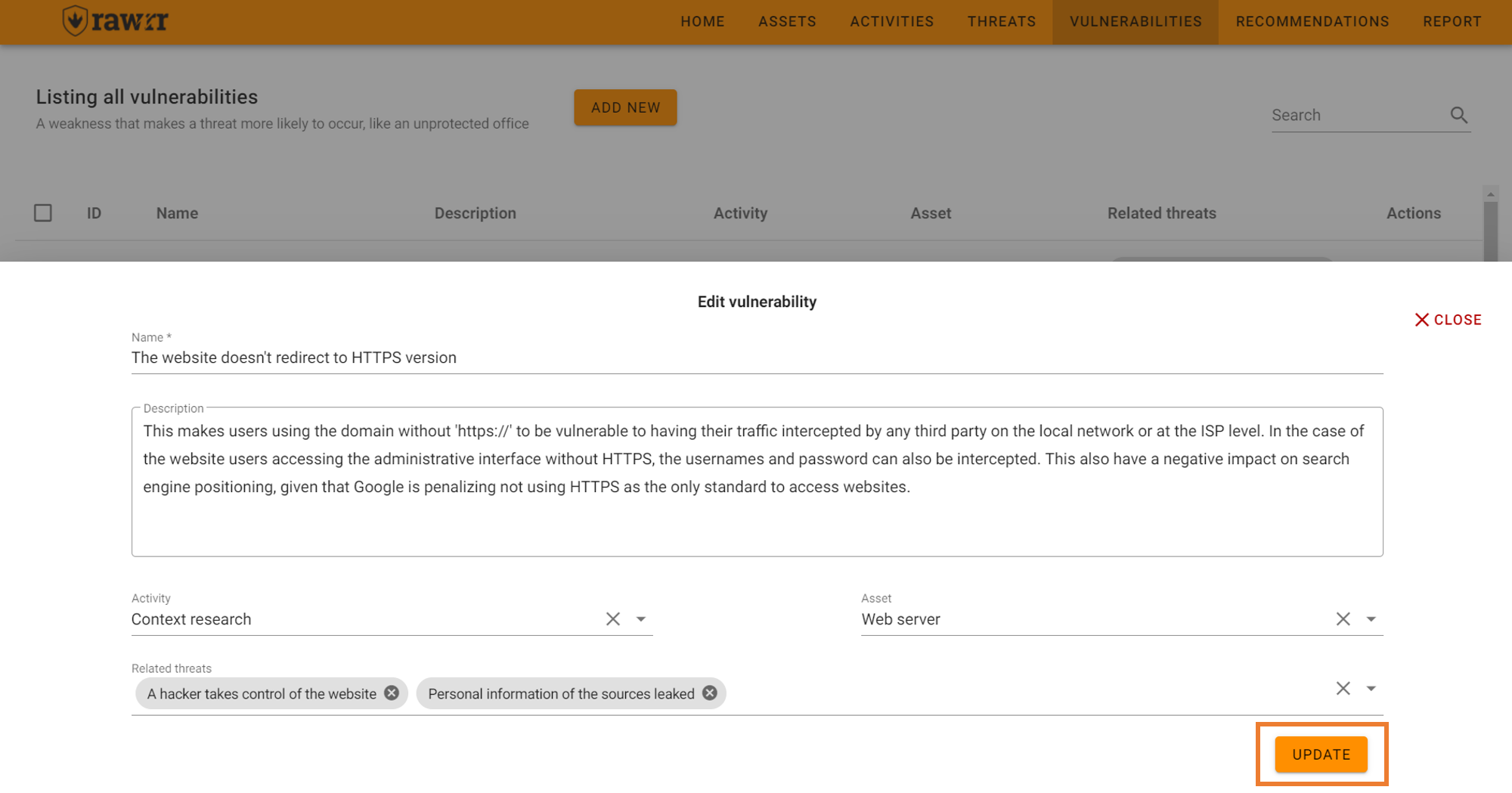
When you finish editing the name, description, threat, assessment activity, and/or asset fields, click “Update” to save the changes to the vulnerability you selected.
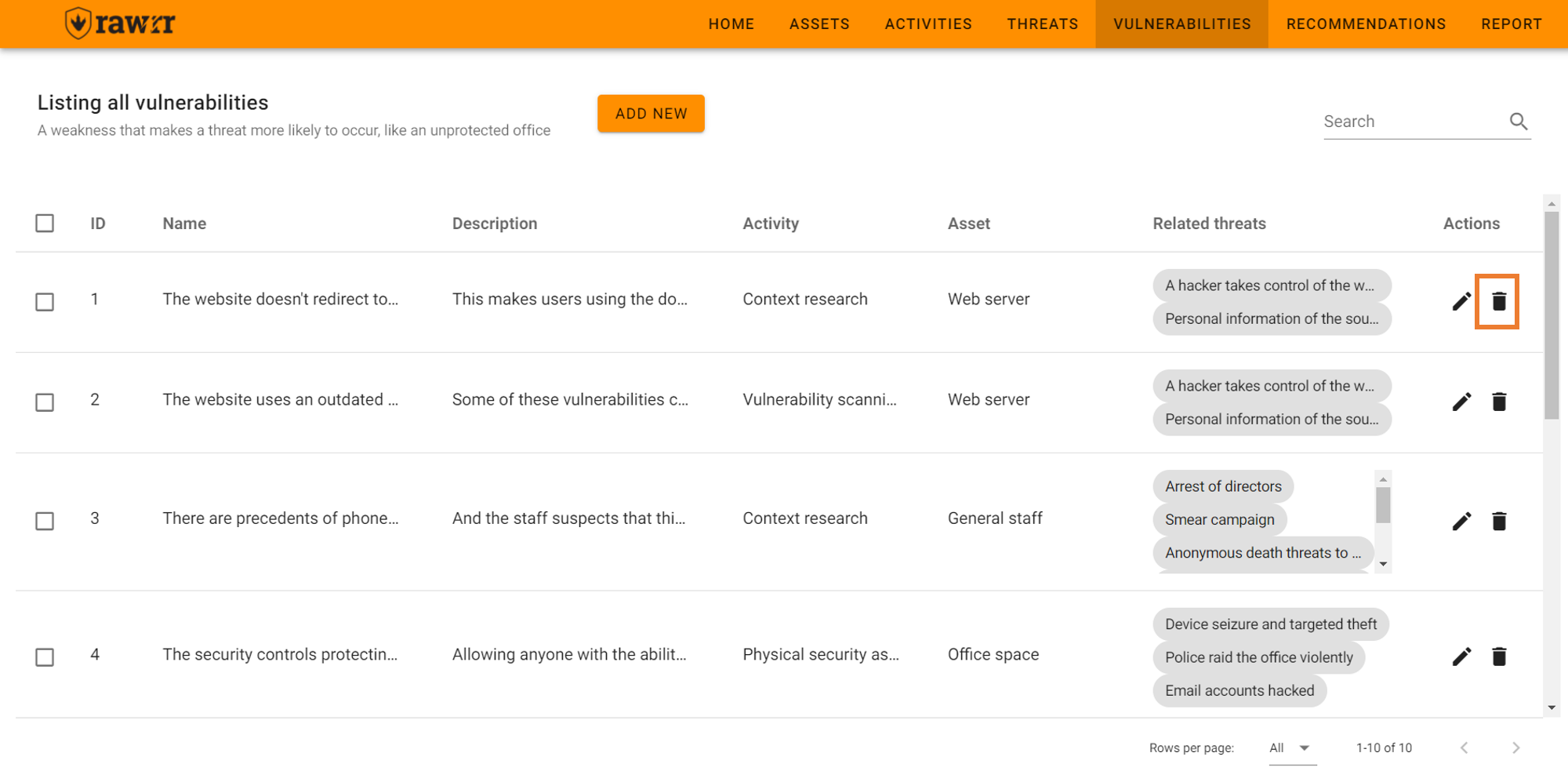
If you want to remove any vulnerability from the list, click on the trash can icon located to the right of each vulnerability that appears in the pre-existing list.
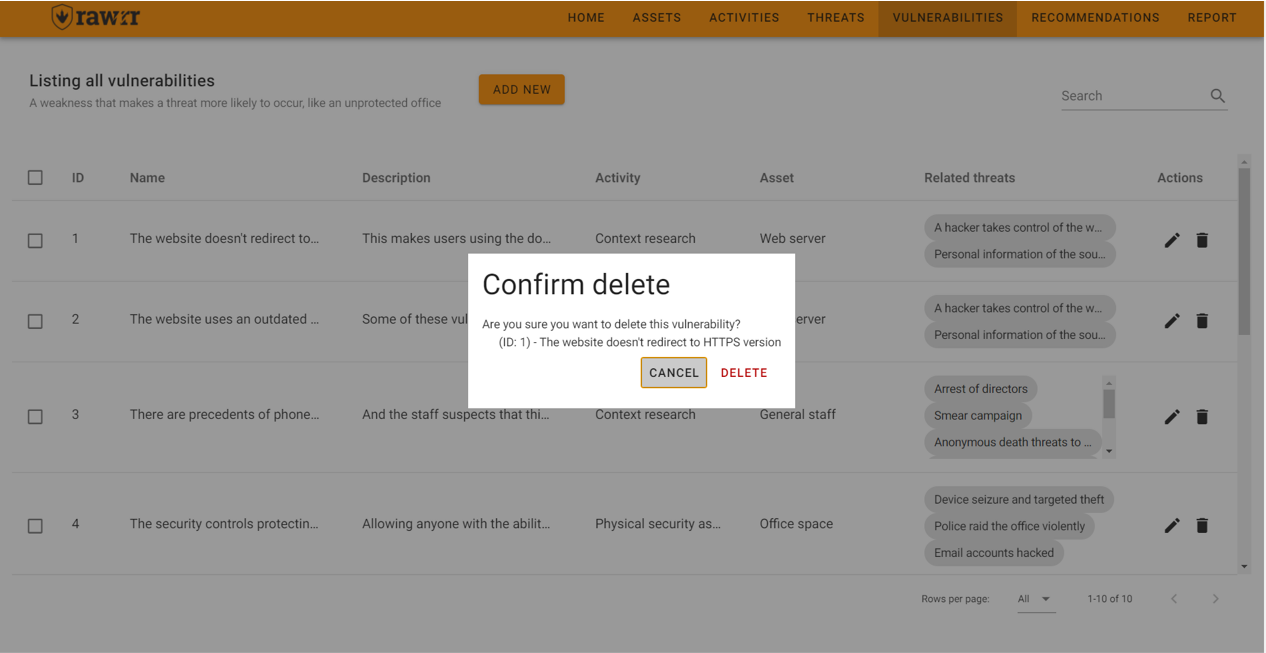
When you click on a confirmation message will appear. If you agree to remove the vulnerability, click “Delete”.
You can also delete various vulnerabilities by selecting them in the left box and then clicking on “Delete Vulnerabilities”.